WhoisXML API’s repository of historical Domain Name System (DNS) lookup records continues to grow in volume and coverage. The DNS database download service has recently been expanded to now include six types of DNS databases:
- DNS A Database
- DNS MX Database
- DNS NS Database
- DNS TXT Database
- DNS CNAME Database
- DNS SOA Database
Each database contains relevant DNS records that enable cybersecurity teams and investigators to conduct extensive threat hunting, cyberforensic analyses, and cybercrime investigations.
DNS Databases Available from WhoisXML API
The six types of DNS databases we offer provide different types of DNS records, namely, A, mail exchanger (MX), name server (NS), TXT, canonical name (CNAME), and Start of Authority (SOA) records.
Each file type is described in detail in the succeeding sections, and more information can also be found here.
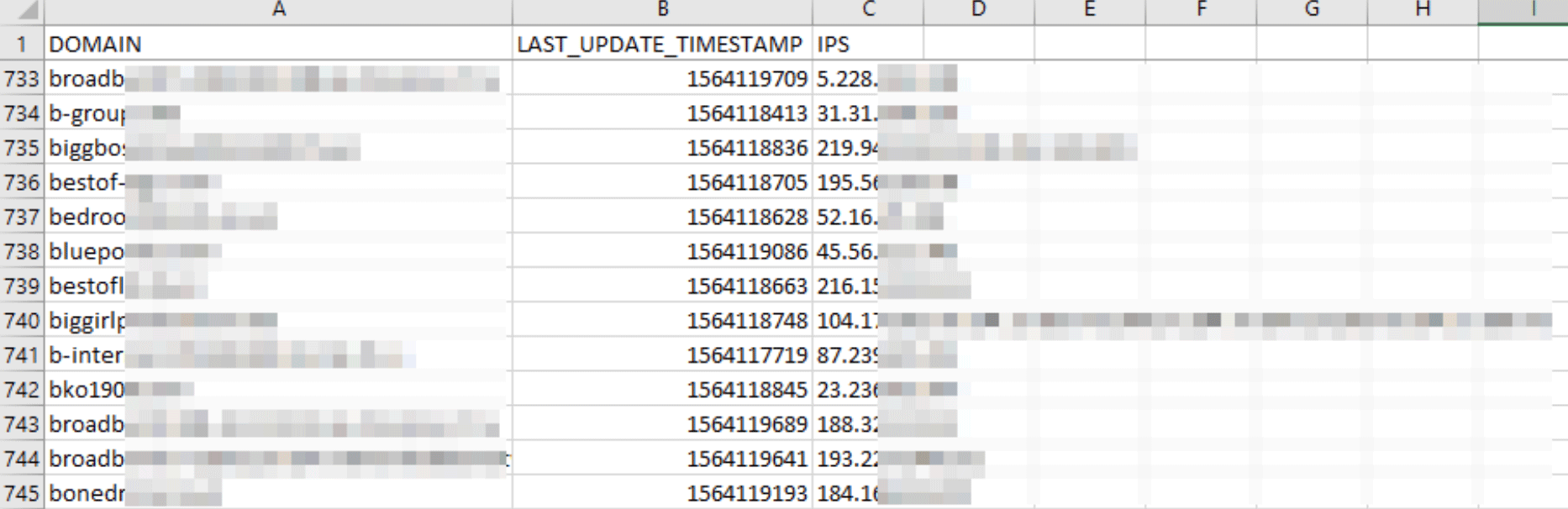
DNS A Database
The A records in the DNS provide the IP addresses that domain names point to. WhoisXML API’s DNS A Database lists down the IP resolutions of domain names. If a domain has multiple IP addresses, all of them will be listed in the third column of the database. The date and timestamp of the A record’s last update would also be reflected in the second column.
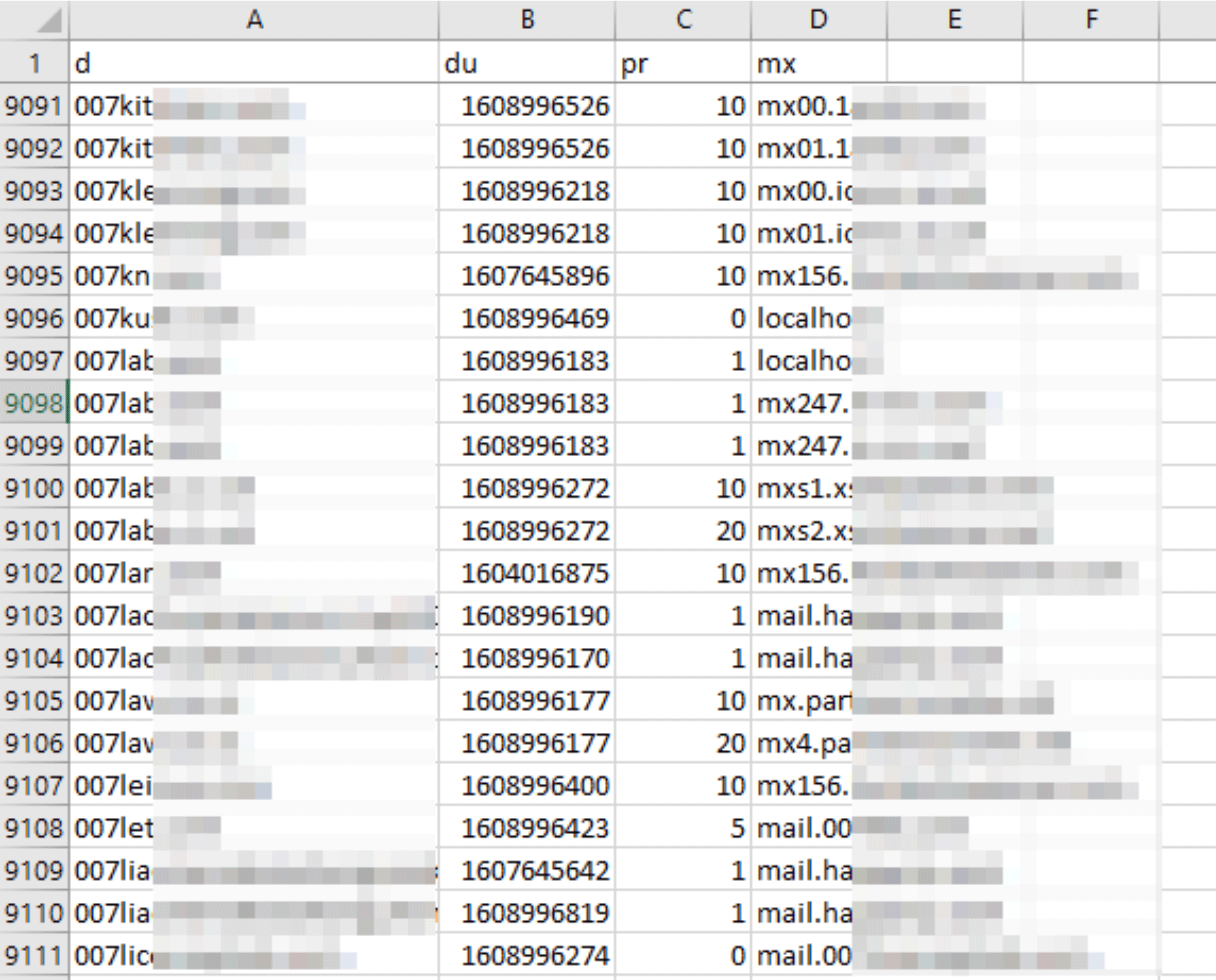
DNS MX Database
MX records determine the mail servers that receive emails on behalf of domains. Administrators can set up multiple MX records to facilitate load balancing and backup mechanisms, requiring them to specify priority or preference numbers. The lower the number, the higher the priority of the mail server.
The domain name, mail server, and mail server priority can be found in our DNS MX Database, along with the date and timestamp when the MX record was last updated.
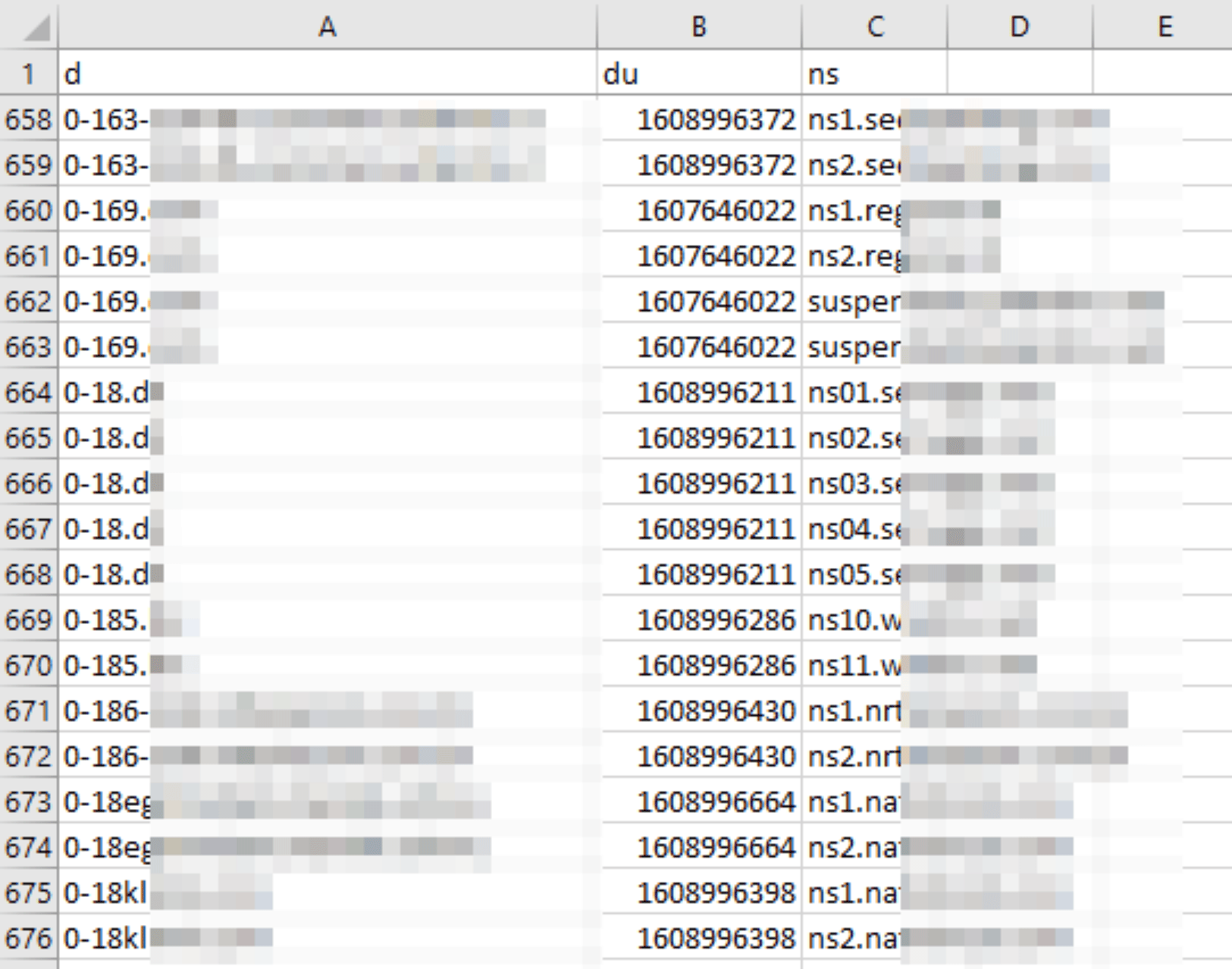
DNS NS Database
The authoritative DNS server that receives queries for a particular domain name is specified in its NS record. WhoisXML API’s DNS database download service includes the NSs associated with domains, along with the date and timestamp when the NS records were last updated. These records are specifically found in our DNS NS Database.
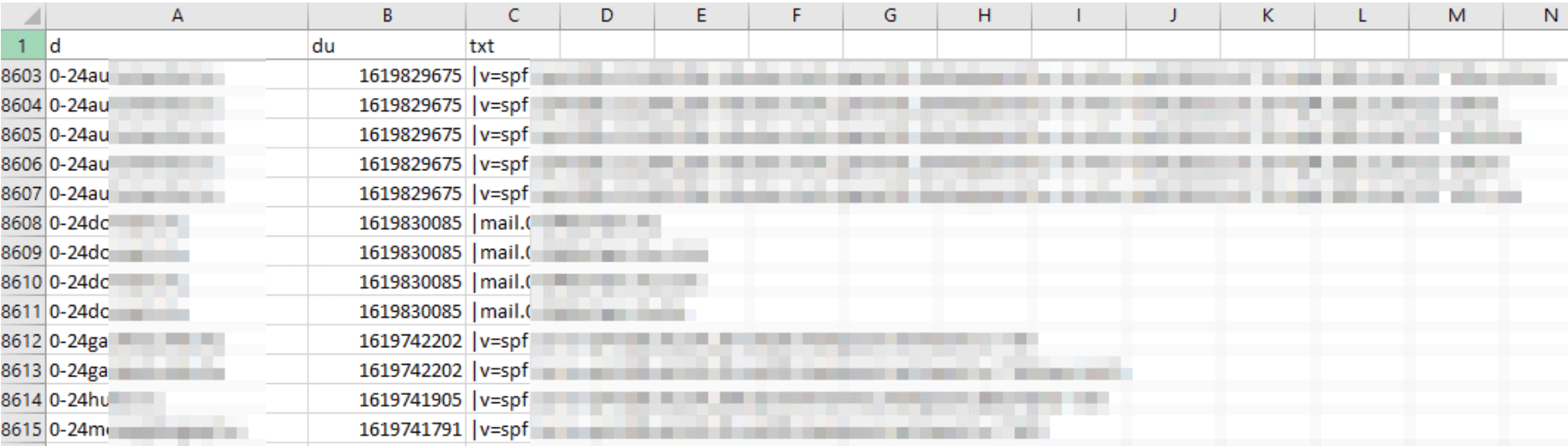
DNS TXT Database
Our DNS TXT Database contains the relevant text information specified by domain administrators. Whether the TXT space is used for Sender Policy Framework (SPF) record; Domain-Based Message Authentication, Reporting, and Conformance (DMARC) authentication; or other details, our database captures them all.
DNS CNAME Database
Our DNS database download service also includes a CNAME database where the aliases of domain names, if any, can be found.
DNS SOA Database
SOA records contain the administrative details about the zones domains belong to, which can help facilitate zone transfers. This data is reflected in our DNS SOA Database, along with the date and timestamp when the SOA record was last updated.
Threat Detection and Mitigation
Among the primary use cases of active and passive DNS databases are threat hunting and detection. Below are some of the threats that the six DNS databases described above can help security teams with.
- Malware: Malware inevitably attempt to contact their command-and-control (C&C) servers. The DNS databases can help analysts see which domains point to known or suspected C&C servers given their IP addresses.
- DNS hijacking: In DNS hijacking, threat actors use malicious techniques to change the DNS settings of victims’ computers. They could change the authoritative name server or IP address to redirect users to websites or applications under their control. Monitoring the DNS A and NS databases could help detect or trace domains whose DNS records may have been hijacked.
- Spam campaigns: The TXT records in the DNS are widely used for spam prevention by making it a space for SPF and other mail authentication standards. Therefore, the DNS TXT Database could enable organizations to see which domains are prone to spamming (i.e., those that don’t use TXT records for authentication).
- Phishing campaigns: Threat actors can make phishing emails look legitimate by forging the sender’s address. SPF and other email validation systems specified in the TXT record can help protect domains’ email sending capabilities from being spoofed and help prevent phishing. Monitoring the DNS TXT Database for domains that don’t have email validation system-related information enables organizations to look out for emails originating from connected domains.
Aside from enhancing security teams’ threat hunting and detection capabilities, the DNS database enrichment can further intensify the capabilities of anti-malware solutions and security information and event management (SIEM); security orchestration, automation, and response (SOAR); and threat intelligence platforms (TIPs).
Are you interested in learning more about our DNS Database Download service? Feel free to contact us here to talk to our team about reinforcing your DNS security capabilities with well-parsed and consistent passive DNS data.