We live in a day and age where an individual’s online security is always at risk. One of the most common types of attacks we see nowadays is phishing. But what exactly is phishing? And how do you protect yourself from it? This article will explain all there is to know about phishing attacks and how to avoid them.
Phishing Definition
Phishing is a social engineering cyberattack that tricks people into revealing sensitive information or deploying ransomware on their devices. These attacks steal user data, including login credentials and credit card numbers.
They trick users into clicking a malicious link filled with malware and ransomware attacks. These links can also trick people into thinking they have trusted pages by using logos of other reputable websites.
This is how these sites can trick users into telling them their sensitive information such as bank credentials, passwords, and personal details. But how do you avoid these kinds of phishing attacks?
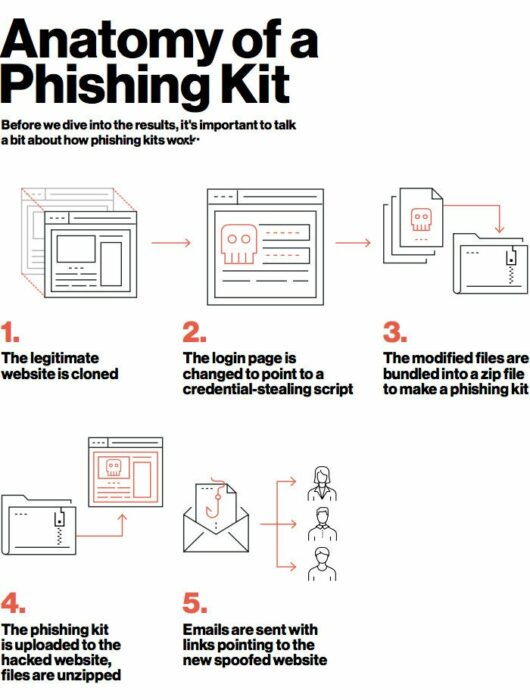
Types of phishing attacks? [examples]
The first step to protecting yourself from these attacks is identifying them. There are many types of phishing attacks out there on almost every form of social media.
Email phishing
In these types of attacks, emails are sent in bulk to many recipients. These emails impersonate different organizations by copying the same phrasing, typefaces, logos, and signatures. This makes them look legitimate, but there are subtle differences that you can spot.
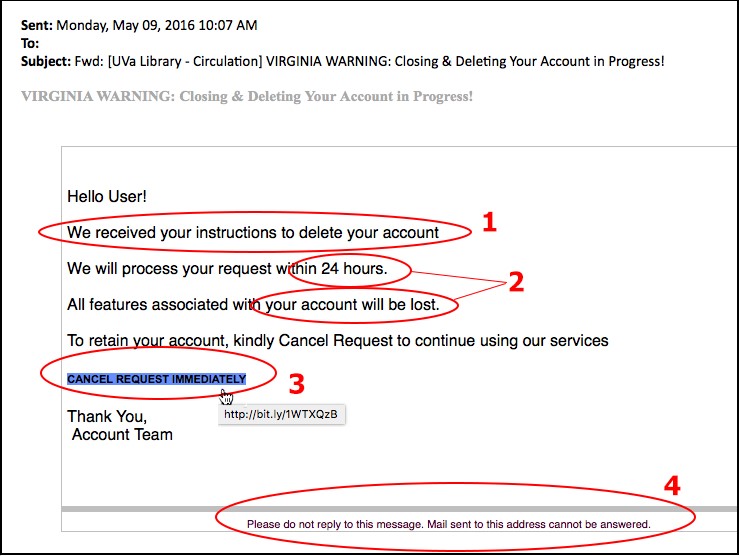
These types of emails are usually time-sensitive to increase the success rates of these attacks. Another way to differentiate them is by looking for misspelled domain names or extra subdomains. E.g. – yesbank.com/payment will be changed to yesbank/payment.com.
Spear phishing
In these types of attacks, specific organizations are targeted rather than the masses. These attacks require particular knowledge regarding the targets to improve the success rate. They often impersonate managers and executives to seem more authentic.
These attacks are of two types:
- Whaling/CEO fraud: Impersonating CEOs and high ranking officials.
- Clone phishing: Copying a previous legitimate email and sending it again after replacing the link with a malicious one.
How to avoid phishing attacks?
- Never open unknown links.
- Two-factor authentication (2FA).
- Check for the correct URL.
- Hover over the link to make sure it starts with “https”.
- Check the source of the message.
What to do if you are a victim of these attacks?
- Make a note of all the information you have shared.
- Activate Two-factor authentication (2FA) if you haven’t already.
- Notify IT support (if you are in an office or school).
- Immediately change passwords on all affiliated accounts.
- Report it to local law enforcement.
How to protect yourself from these attacks at all times
You can avoid most phishing attacks by following the steps above and being vigilant. Do not carelessly open any link and think twice before giving away your personal information.
You can also use a browser with suitable security protocols. Most browsers already have a list of malicious websites that steal user information and actively block them. Make sure to follow all the tips given in this article to keep yourself secure.





