[ad_1]

Data breaches at major organizations are continuously raising cybersecurity concerns.
But, understanding the anatomy of a cyber attack can help in finding methods to potentially reduce the impact of cyber threats.
A data breach at Cathay Pacific Airlines Ltd compromised the data of 9.4 million customers. The compromised data included personal information, credit and debit card details, passport details, frequent-flier programs, and historical travel information. The attack is considered as the biggest airline data breach. And, the customers feel betrayed as the officials disclosed the attack seven months after finding out the unauthorized access.
Similarly, many organizations are attacked for sensitive data or ransom. And, hackers are consistently working on new malware and cyber attack techniques to find loopholes in current cybersecurity standards. Hence, every organization is prone to cyber threats. To prevent these attacks, organizations must first understand the anatomy of a cyber attack, and the motives behind it.
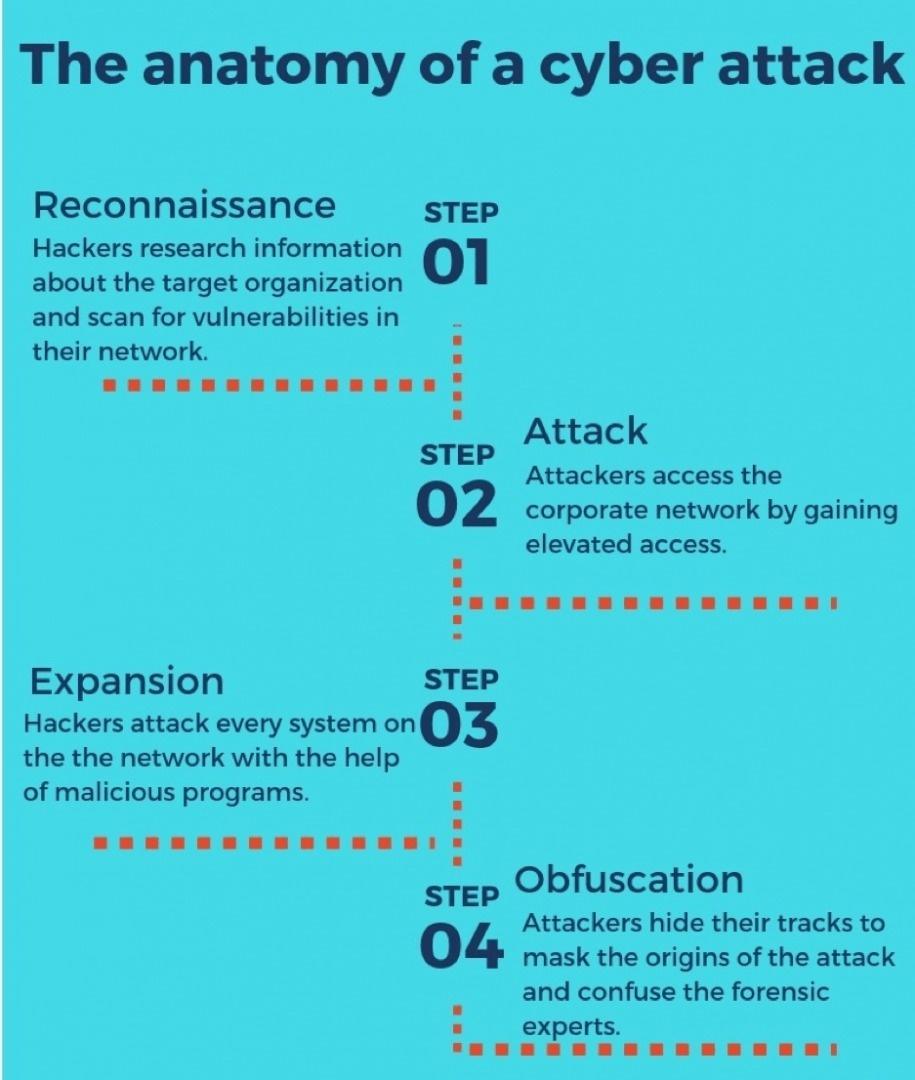
The Anatomy of a Cyber Attack
Step 1: Reconnaissance
The first part of the anatomy of a cyber attack is reconnaissance. Hackers usually start by researching and gathering information about the target organization. They look for network ranges, IP addresses, and domain names. And, hackers also search for email addresses of key players in the organization such as CFOs, IT professionals, and CTOs. If the hackers fail to find the email addresses of key players, then they identify vulnerable employees by sending phishing emails. Next, the attackers scan for vulnerabilities in the network, which is a long process, that sometimes, take months. After they get an entry to the organization via network vulnerabilities or employee email address, attackers proceed to the next phase.
Step 2: Attack
After getting access to the network, a hacker proceeds to infiltrate the organization’s network. But, to access the network freely, the attacker needs access privileges. Hence, attackers use rainbow tables and similar tools, which help them in stealing credentials to upgrade their access to administrator privileges. Now, hackers can access the entire network, and go through the network silently. Then, attackers are free to obtain sensitive information for selling on the internet or encrypt the data to demand ransom. Sometimes, hackers may also alter or erase sensitive data for reasons beyond financial gain.
Step 3: Expansion
The next phase of the anatomy of a cyber attack is expansion. Hackers intrude all systems on the network using malicious programs. Malicious programs enable attackers to hide in multiple systems in the organizations and regain access to the network even after being detected. Additionally, hackers no longer require higher access to infiltrate the network.
Step 4: Obfuscation
Hackers proceed to hide their tracks to mask the origins of the attack. Additionally, the attackers safely place their exploit in a system to avoid getting detected. The main purpose of obfuscation is confusing and disorienting the forensic experts. For successful obfuscation, hackers use various tools and techniques such as spoofing, log cleaning, zombied accounts, and Trojan commands. Cybersecurity experts generally consider obfuscation as the final stage of the anatomy of a cyber attack.
Understanding the Motive Behind Cyber Attacks
To effectively protect your organization from cyber attacks, it is essential to understand the motive behind cyber attacks. The motives of a hacker can help find flaws in the anatomy of a cyber attack. For example, the WannaCry ransomware was recently used to attack several hospitals and GP clinics all over the United Kingdom, which cost the NHS almost £92m. The attackers exploited a leaked NSA tool to attack vulnerable Windows systems and encrypt sensitive information. Furthermore, the attack canceled over 19,000 appointments. Similarly, ransomware is used by attackers to encrypt vital information and extort ransom in exchange for decrypting data. Another reason could be cyber terrorism to create fear among the masses. Alternatively, major cyber attacks can also serve as a distraction for something darker behind the curtains.
Preventing Organizational Cyber Attacks
To protect the organization, business leaders such as CIOs and CTOs need to hire skilled cybersecurity professionals. Cybersecurity experts spend years in researching and studying the anatomy of a cyber attack, and they know how to prevent or at least minimize the impact of cyber attacks. Cybersecurity experts can maintain the security standards in your organization through multiple steps and measures such as follows:
- Cybersecurity experts test the systems and the network for vulnerabilities and fix them preemptively.
- Intrusion prevention technology is capable of detecting reconnaissance attempts. And, URL filtering and reputation-based security services can block suspicious links that may contain viruses or malware.
- Cybersecurity experts install firewalls and malware scanners to block malware and viruses. Malware is constantly redesigned by attackers to avoid being detected by traditional signature-based systems. Hence, advanced persistent threat protection needs to be used to detect malware based on malware behavior.
- Organizations need to pay close attention to the outgoing traffic and apply egress filter to monitor and restrict outgoing traffic.
- Cybersecurity experts must conduct regular audits of hardware and software to monitor the health and security strength of their IT systems.
- Organizations should consider training employees and educating them about cyber attacks as one of their top priorities.
Creating Damage Reduction and Recovery Strategies
Organizations have to realize that even after following all the security protocols, hackers can still attack their networks and systems. With the help of cybersecurity experts, organizations can analyze the anatomy of a cyber attack to find flaws in the attacks, and exploit the weaknesses to reduce the damage. Various organizations only plan for protection from cyber threats, completely avoiding recovery mechanisms, which can lead to dire consequences in case of an attack. For example, Google is shutting down Google+ due to a data breach that compromised 500,000 user accounts in 2015. But, Google announced that they became aware of the breach during March and June 2018. Learning from the example of Google, organizations should know the importance of minimizing the damage. To reduce the damage from cyber attacks, organizations should consider the following steps:
- The first step would be encrypting all the data that your organization owns. Even if an attacker infiltrates the network, decrypting the data will need hours, which may buy some time for the security experts to find the source of the attack.
- Organizations must adopt two-factor authentication system, as passwords can get leaked easily. With two-factor authentication, the attacker cannot access the data even after acquiring the leaked passwords.
- For better data loss prevention, cybersecurity systems should set up alerts for outgoing data. The alerts can notify the organization about their data being stolen after a data breach.
- Hackers control the systems and networks with malware-based communication systems. Hence, blocking outgoing command and control connections can effectively stop outgoing malware communication.
Applying Modern Technologies for Better Cybersecurity
Artificial intelligence is playing a pivotal role in cybersecurity. Machine learning has the ability to analyze the anatomy of a cyber attack, and learn from the behavior patterns of malware. Moreover, artificial intelligence can automate threat detection and data recovery mechanisms. Hence, AI-powered applications can find security threats and implement recovery strategies more efficiently when compared to software-based solutions. And, big players such as Microsoft, Google, Palo Alto Networks, Fortinet and Cisco Systems are already developing cybersecurity solutions using artificial intelligence and machine learning. With the exponential development of artificial intelligence, numerous security software have started adopting machine learning to provide more effective cybersecurity solutions.
Likewise, blockchain technology has the potential to improve cybersecurity. Blockchain can effectively detect a data breach, and disrupt the process that forms the anatomy of a cyber attack. With blockchain, organizations can distribute their data over the network, which will simplify the process of data recovery. And, the changes in data would be transparent. Hence, if the data is altered or deleted, tracking the changes will be an easy process. Furthermore, multiple cybersecurity firms are working on developing blockchain-powered security solutions for mainstream applications. For example, Acronis, a cybersecurity organization, is applying blockchain technology to generate a cryptographic hash, that is unique for every data file. The hash can be used to verify the authenticity of every file. And, it is almost impossible for a hacker to compute the cryptographic hash. Thus, AI and blockchain are revolutionizing the cybersecurity landscape.
Although the technology and methods to fight cyber attacks are getting better, hackers are also developing their techniques to execute stronger attacks. And, with new malware and ransomware being developed, these attacks can lead to bigger data breaches than any we’ve seen before. Hence, organizations need to become aware of the anatomy of a cyber attack to be able to tackle cybersecurity issues better.