Fraud Management & Cybercrime
,
Ransomware
Two Companies Have REvil Data. They Don’t Appear Eager to Help.

Threat intelligence researchers are looking closely at REvil, the ransomware gang that last week infected up to 1,500 companies and organizations in a single swoop. A look at part of the group’s online infrastructure shows clear lines to Russian and U.K. service providers which in theory could help law enforcement but don’t appear eager to help.
See Also: Live Panel | Zero Trusts Given- Harnessing the Value of the Strategy
On July 2, actors affiliated with REvil exploited several vulnerabilities in remote management software called the Virtual System Administrator, which is made by Miami-based software developer Kaseya.
The U.S. is pressing Russia for more cooperation in cracking down on ransomware criminals the U.S. alleges the country harbors. Pulling the threads around the decoder[dot]re domain might be a good place for the two countries to start.
The vulnerabilities, combined with a series of clever maneuvers, allowed REvil to distribute ransomware to up to 60 Kaseya customers, which are mostly managed service providers. Once on those MSPs systems, REvil used VSA to push ransomware down to their customers, which included small businesses and municipalities (see Kaseya: Up to 1,500 Organizations Hit in Ransomware Attack).
The damage may not be as bad it could be, as the attackers didn’t delete Volume Shadow Copies, a Windows backup feature. One MSP in the Netherlands, VelzArt, reported on its blog of successful efforts restoring their customers’ systems, albeit with very long days on the job.
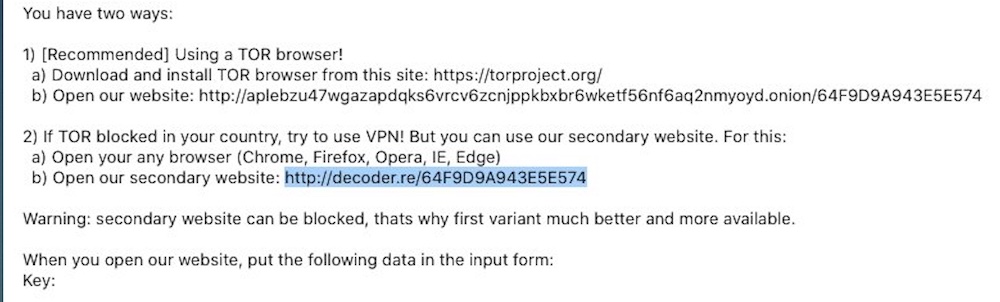
Still, some infected organizations have been negotiating ransom payments with REvil via the group’s web-based customer service portals. And one of those portals has been left with fewer protections, which in theory could help law enforcement.
Ransom Chat Portal
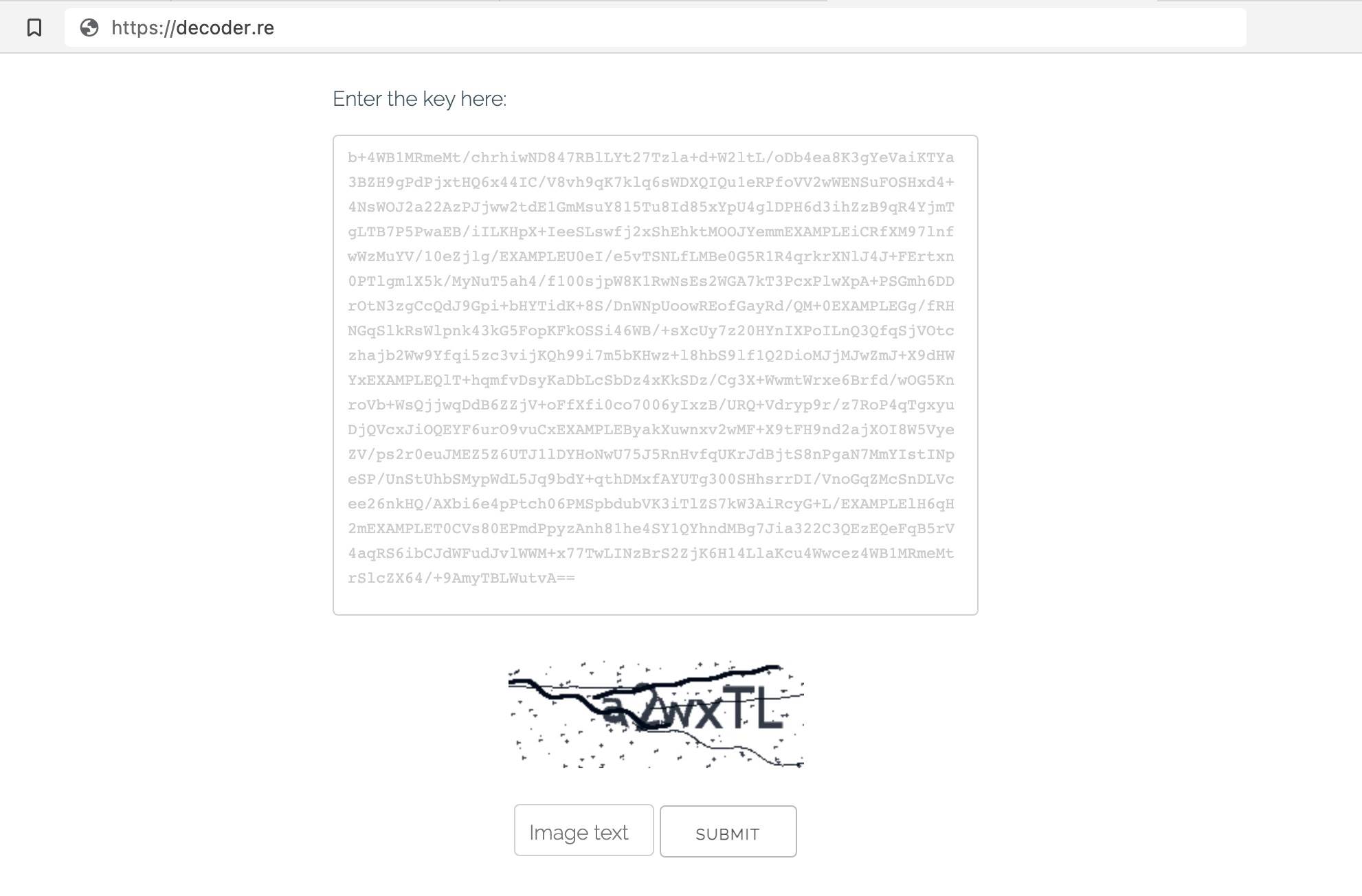
To start the process, victims go to a website with their assigned user ID. Then, a victim enters a private key found in their ransom note, which brings up a chat dialog, the ransom being demanded and the time left before the ransom rises due to non-payment.
REvil typically creates those customer service sites using the Tor anonymity system, which is short for The Onion Router. With Tor, it’s possible to set up a so-called “hidden” website that masks the normal technical information. It’s near impossible to figure out where a hidden site is actually hosted.
But REvil has also set up a regular website, decoder[dot]re, for negotiations in case Tor is blocked in a particular country. The site, which is hosted in Russia, has been included in ransom notes found in REvil ransomware victims since at least January, says Gene Yoo, chief executive officer of Los Angeles-based Resecurity, which investigates cybercrime and data breaches.
“It is obvious that the Russian government can’t not be aware about this malicious activity,” Yoo says. “These details add clear connections between REvil and Russia. Hopefully, it will be properly investigated to contain this malicious activity damaging the business of thousands of companies globally.”
After meeting with President Joe Biden in mid-June, Russian President Vladimir Putin dismissed accusations that Russia’s IP space was the source of major cyberattacks, says Alex Holden, CTO of Hold Security, a Wisconsin-based threat intelligence company.
“It is not a valid technical comment,” Holden says. “Here we see another example of crime emanating from Russia.”
Clearnet Mirror
Because the site is on the clearnet, Resecurity as well as other researchers have been looking into its network addresses and DNS records, which reveal several touch points that investigators could query.
Of course, domain name registration information can be faked and hosting can be purchased anonymously. But at the same time, threat actors have been known to make glaring operational security mistakes, and even a slip up in something as minor as re-using an email address can unravel an online mystery, as the investigation into the Silk Road online market showed.
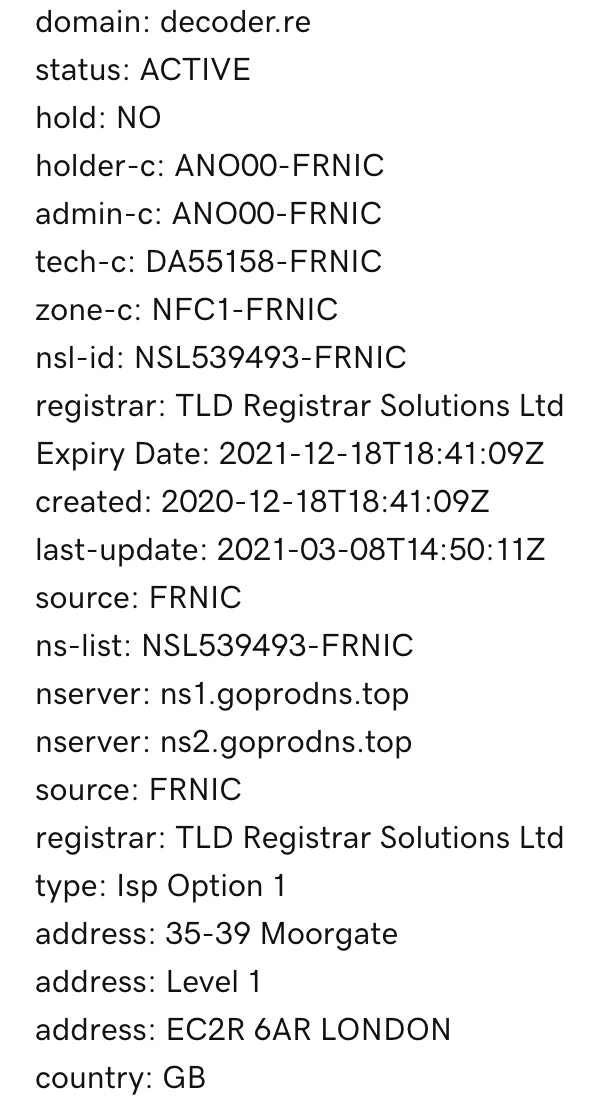
Decoder[dot]re appears to have been purchased on Dec. 18, 2020, from TLD Registrar Solutions, which is based in the U.K., according to RiskIQ’s Reputation Lookup database.
Passive DNS records show the domain has been hosted since January by a Russian IT services company called JCS IOT, which develops internet-of-things solutions and offers cloud hosting services, virtualization and dedicated servers. JCS IOT also seems to be the parent company for a Russian hosting provider called FirstVDS. The two companies have the same legal entity as an owner and contact address.
The primary DNS record resolves to 82[.]146.34.4 which is an IP hosted in Russia that has been linked to various other REvil operations, writes Ryan Sherstobitoff, vice president of Cyber Threat Research and Intelligence with SecurityScorecard, a New York-based cybersecurity company.
Sherstobitoff tells me the cybercriminals behind the server have invariably used fake names. But there could be interesting information on the server, such as victims that the attackers have communicated with and possibly a Jabber server they use for their own chats, he says.
“We’re also looking at where these guys actually operate,” Sherstobitoff says. “These investigations are difficult for sure.”
In the past couple of years, REvil has used other clearnet domains as secondary channels for its negotiating portals, including decoder[dot]cc and decryptor[dot]top. Those domains, however, are no longer active, and it appears decoder[dot]re is the replacement.
Decoder[dot]re is definitely affiliated with REvil, as it is a precise mirror of the Tor hidden portals used for negotiations, Yoo says. Using available ransomware samples and information collected from the victims, it’s possible to log into victims’ negotiation pages. Entering a message in the chat on decoder[dot]re can then be seen when logging into the same victim’s chat window via one of REvil’s Tor hidden negotiating portals.
JCS IOT has an email address dedicated for accepting abuse complaints. I emailed that address along with others affiliated with the company and the associated company, FirstVDS. Neither has responded to emails sent in Russian and English.
Registrar Responds
However, TLD Registrar Solutions, which sold the domain name registration, did respond. But it immediately became clear the company isn’t in a hurry to revoke the registration.
The response to my email came from someone named Lexie Kluss, who is on the support team of another domain name registrar registered in the Bahamas called Internet.bs.
According to Internet.bs’s terms and conditions, TLD Registrar Solutions Ltd. is its parent company. TLD is listed as an accredited entity with the Internet Assigned Numbers Authority, the organization that oversees internet addressing and protocol issues.
To add another complicating layer, Internet.bs has been owned since 2014 by the CentralNic Group PLC, which is listed on the London Stock Exchange.
Kluss writes that an investigation found it could take no action. Kluss writes that Internet.bs does not host the content, which is indeed true, and that the issue should be taken up the decoder[dot]re’s hosting provider.
Incredibly, Kluss also writes that the company would comply with a law enforcement order for a revoking the registration but that: “We feel that this type of request is a temporary resolution and not reflective in value of the risk associated with the act of interrupting the DNS for us as a Registrar. By registering another domain with another Registrar any registrant can reinstate their content within a matter of minutes.”
Kluss continued: “Due to the time and cost to Internet.bs to review all of the legal issues, we respectfully ask that you provide evidence to show that you have attempted to address these issues with the above-mentioned hosting providers without result before we re-investigate what actions, if any, we are able to take.”
To paraphrase: Whomever is running the site will just go to another registrar, so why bother?
Take It Offline?
Whether decoder[dot]re should be taken offline does raise a question.
The portal is likely being used by organizations to communicate with their attackers. Although whether or not to pay ransoms is a contentious point of debate, it also wouldn’t help to make it more difficult for organizations already struggling with an infection to not have all options available, including paying for a decryption tool if it comes down to that.
The U.K. registrar should be easy for law enforcement to query. The Russian hosting company, JCS IOT, is obviously harder. As Sherstobitoff says, those involved in the attack are using Russia as a safe haven.
The U.S. is pressing Russia for more cooperation in cracking down on ransomware criminals the U.S. alleges the country harbors. Pulling the threads around the decoder[dot]re domain might be a good place for the two countries to start cooperating in earnest. At least in theory.