[ad_1]
Amnesty International has detailed evidence showing some of the ways NSO’s Pegasus spyware tool infiltrated the iPhones of journalists and activists, by using weaknesses in Apple’s software including an iMessage zero-click 0-day vulnerability.
On Sunday, an investigation was published claiming the Pegasus tool created by NSO Group was being used by governments to attack critics and journalists. While NSO claimed the tool was only to be used against criminals, a leaked list of potential targets revealed a number of journalists were also being monitored by NSO’s clients.
In a report breaking down the forensic evidence left behind by Pegasus, Amnesty International’s Security Lab shows off a number of traces that reveal a Pegasus attack was attempted on iPhones and other smartphones. For many of the attacks, it appears that NSO used vulnerabilities within Apple’s software to gain access.
Amnesty describes the detailed attacks as running from 2014 up until July 2021. Some of the attacks were deemed “zero-click,” where a target doesn’t have to interact in a specific way to be successfully attacked.
Multiple zero-day vulnerabilities are also used, including one instance of attacking a fully-patched iPhone 12 running iOS 14.6 in July.
Attacks listed in the report began as early as May 2018.
Network injection
The first category of attack is network injection, where users are mysteriously redirected from one legitimate website to another. Logs in Safari’s browsing history revealed suspicious URLs being visited, evidence of a redirect that occurred barely a second after opening a webpage.
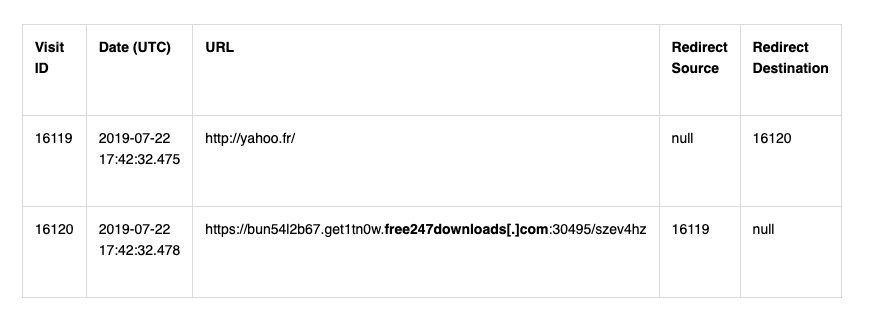
Favicon databases also showed evidence of similar redirects, though not necessarily via active browsing. In one case, the Safari View Service used when previewing a link shared in a journalist’s Twitter timeline prompted the webpage load and redirect to the suspicious URL, despite not opening a separate browser.
Bridgehead
Records of process executions revealed processes called “bh,” which have also been linked to Pegasus installation domains, usually appearing just after a successful network injection attempt.
It is believed the “bh” relates to a 2016 vulnerability in the iOS JavaScriptCore binary, which enabled code execution and to maintain a persistence on the device post-reboot. The “bh” is thought to stand for “BridgeHead,” an internal name for the component.
After “bh,” other processes are used, including “roleaboutd” and “msgacntd,” which are believed to be later-stage processes used after a successful exploitation and privilege escalation. Other similar processes have been found, including “pcsd” and “fmId,” which may have the same purposes.
Photos
A potential exploit in Photos may have been used in attacks, with evidence showing an Apple process for the Photos app called “mobileslideshow” was used before the “bh” process was employed.
It is suspected that the Photos app or Photostream service were used as part of an exploit chain to deploy Pegasus.
In each of the cases where Photos was used, it appears the same iCloud account address was used with Photostream. Purpose-made iCloud accounts are apparently required for some of the “zero-click” attacks to work.
Zero-click 0-days in iMessage
From 2019, numerous vulnerabilities were discovered and patched in iMessage and FaceTime, but it seems that some issues were still available for abuse.
In one attack, it was discovered suspicious iMessage account lookups were followed by the execution of Pegasus processes. Multiple Hungarian journalists were apparently the target of the same operator, with similar addresses and processes used across each of the attacks.
The attacks via iMessage apparently returned in 2021, this time involving a lookup of a suspicious iMessage account, followed by a HTTP request performed by a coretelephony process. This seemed to request a payload for a process titled “gatekeeperd.”
An attack from May 2021 revealed a similar lookup for a mystery iCloud account, though it was then followed by at least 20 iMessage attachment chunks created on the iPhone’s storage. Push notifications were apparently used as a way to apply the payload to the target iPhone before execution.
Apple Music
Evidence has also been found that Pegasus could have been delivered via the Apple Music app in July 2020. For that infection, network traffic for Apple Music was recorded, with a HTTP request by the Music app again pointing to domains used to distribute Pegasus.
Amnesty couldn’t determine if Apple Music itself was exploited for the initial infection, or if it was used for sandbox escape or privilege escalations.
Following the investigation, Amnesty has released Pegasus indicators via GitHub to assist other security researchers in finding other Pegasus infections. The indicators include domain names in the Pegasus infrastructure, email addresses recovered from iMessage account lookups, and process names linked to the software.
A tool is also being released called the Mobile Verification Toolkit. A modular tool, it aims to simplify the process of acquiring and analyzing data sourced from Android devices, as well as analyzing records from iOS backups and system dumps, to find any further potential traces.
Little risk to normal users
The details of Pegasus demonstrate that there are still areas of concern in Apple’s mobile operating system that need continuous improvement and monitoring. The fact that the report details attacks over multiple years, to as recent as July 2021 indicates the software is still being used, and continues to pose a risk.
The determination that attacks in July occurred against a fully-patched iPhone 12 running iOS 14.6 is especially worrying, as that shows some security holes are still open and need to be closed.
However, it is unlikely that Pegasus will be a problem for the vast majority of iPhone users. While the tool is used as intended against criminals by governments, the attacks against innocent people are seemingly against those who could be critics to a regime, including journalists and human rights activists.
Pegasus is concerning, but unless you happen to be a major critic of a government, you probably won’t be a target of the spyware tool.
Keep up with everything Apple in the weekly AppleInsider Podcast — and get a fast news update from AppleInsider Daily. Just say, “Hey, Siri,” to your HomePod mini and ask for these podcasts, and our latest HomeKit Insider episode too.
If you want an ad-free main AppleInsider Podcast experience, you can support the AppleInsider podcast by subscribing for $5 per month through Apple’s Podcasts app, or via Patreon if you prefer any other podcast player.




